I rented small servers on digital ocean in different regions. I didn't use them for anything, but I made them listen to all the failed login attempts made on the machine. Before reading the next bit, this might be a good time to stop and ask yourself: how bad is it?
I used a simple tool to measure bad logins named fail2ban. It is a daemon that logs login attempts and it blocks anyone who surpasses a number of failed ones. You can find a tutorial on the tool here.
Results
Here's the histogram over time:
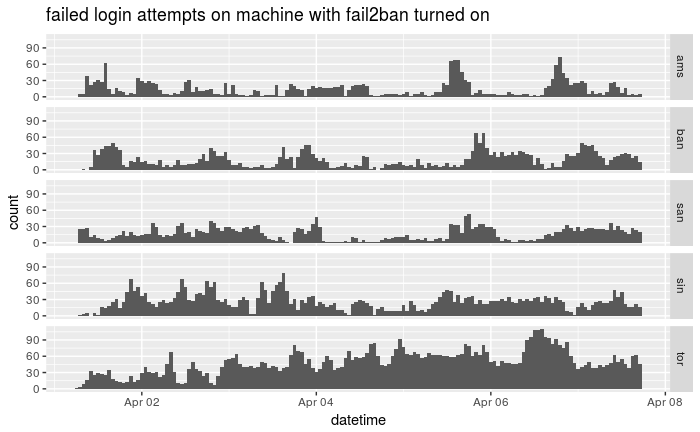
In total it seems that Toronto got targeted more and Amsterdam got less. One should remember that we block a lot of traffic because of fail2ban but in a week I saw this many failed logins per machine:
toronto-auth 7691
singapoore-auth 4110
bangalore-auth 2920
sanfransisco-auth 2643
amsterdam-auth 2266
These login attemps could all be done by the same person, a few people but it doesn't seem likely that these are all different people. An interesting observation is that these attemps seem to correlate over time.
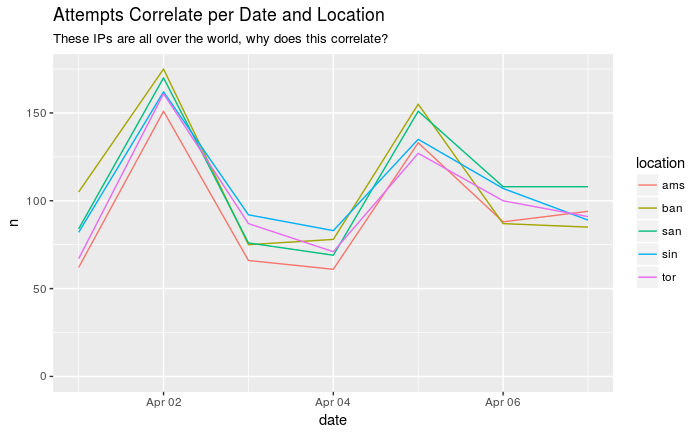
That's a lotta blocked traffic. When first looking around the data I got a bit frightened too. There were login attempts with the username vincent. How could people guess this?
After checking the ssh usernames that were being used I found out that this was just a guessing game. Here's the top guesses;
101 sentry support alex wp-user teamspeak
admin pi serverpilot odoo james john
user git sammy rails temp wp-admin
test deployer guest sybase ftp andrew
postgres www tomcat musicbot docker qhsupport
oracle sshvpn hduser castis jboss jira
ubuntu testuser zabbix ftp_user demo cron
ftpuser hadoop ftp_test webmaster user1 server
deploy mysql minecraft zimbra frappe bot
jenkins nagios 1234 test1 squid butter
Later in the list you see more 'human' names appear like mine. It seems like script kiddies have a list of login names that are common and just try them all. I was somewhat suprised that minecraft made it up in the list.
Lesson
These are just ssh attempts. There's other stuff you might need to be concerned about;
- jupyter notebooks
- rstudio servers
- wordpress
- django admin
If you're running stuff on the web. Know that people are at least trying to find an easy weakness, about 2000 times a week.